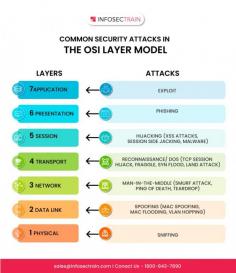
Have you considered how cyber-attacks target various layers of your network? Here’s a look at some common vulnerabilities:
Application Layer : This layer is susceptible to exploits where attackers leverage software vulnerabilities.
Presentation Layer : Phishing attacks can deceive users into disclosing sensitive information, putting data security at risk.
Session Layer : Be cautious of hijacking, where attackers can take control of user sessions, gaining unauthorized access.
Transport Layer : Reconnaissance attacks collect information about your system, often paving the way for larger and more damaging assaults.

